
 |
Eterlogic virtual serial ports emulator |
Important: in case of connectivity issues please configure firewall rules for EterlogicVspeDeviceManagerService.exe located in VSPE program folder on server and client computers. Please note that by default TCP connection is not encrypted. To encrypt traffic, configure TLS security settings.
If you do not want to forward modem registers (RTS/DTR etc), You can ignore Control port settings
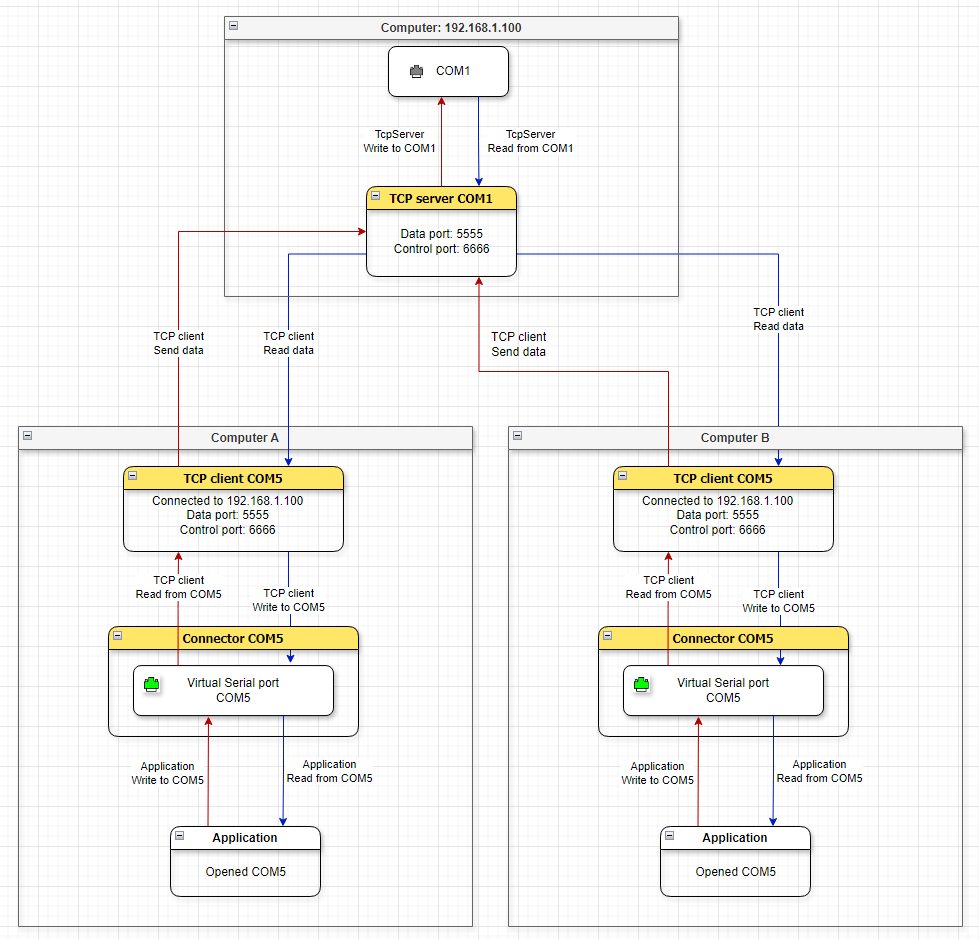
Data flow diagram
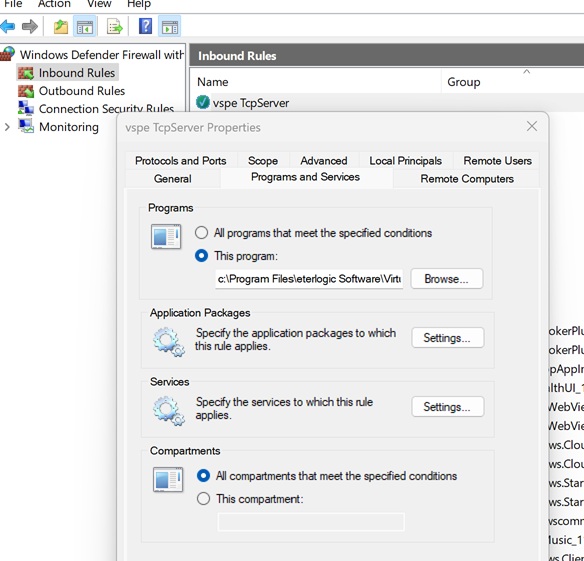
Inbound rule
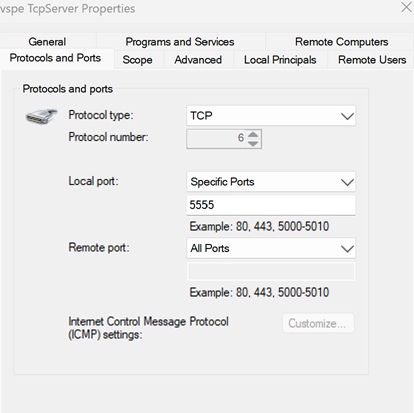
Specifying inbound rule protocol and TCP port
Example: allowing VSPE to listen on specific TCP ports (5555 and 5556) and accept incoming connections from all remote IP addresses
New-NetFirewallRule -DisplayName "VSPE TcpServer" -Direction Inbound -Program "C:\Program Files\Eterlogic Software\Virtual Serial Ports Emulator (x64)\EterlogicVspeDeviceManagerService.exe" -Action Allow -Profile Any -Protocol TCP -LocalPort 5555,5556
Example: allowing VSPE to listen on specific TCP ports (5555 and 5556) and accept incoming connections only from specified remote IP addresses (192.168.1.100 and 192.168.1.101)
New-NetFirewallRule -DisplayName "VSPE TcpServer" -Direction Inbound -Program "C:\Program Files\Eterlogic Software\Virtual Serial Ports Emulator (x64)\EterlogicVspeDeviceManagerService.exe" -Action Allow -Profile Any -Protocol TCP -LocalPort 5555,5556 -RemoteAddress 192.168.1.100,192.168.1.101
Example: allowing VSPE to listen on all TCP ports and accept incoming connections from all remote IP addresses
New-NetFirewallRule -DisplayName "VSPE TcpServer all ports" -Direction Inbound -Program "C:\Program Files\Eterlogic Software\Virtual Serial Ports Emulator (x64)\EterlogicVspeDeviceManagerService.exe" -Action Allow -Profile Any -Protocol TCP
Example: allowing VSPE to listen on all TCP ports and accept incoming connections only from specified remote IP addresses (192.168.1.100 and 192.168.1.101)
New-NetFirewallRule -DisplayName "VSPE TcpServer all ports" -Direction Inbound -Program "C:\Program Files\Eterlogic Software\Virtual Serial Ports Emulator (x64)\EterlogicVspeDeviceManagerService.exe" -Action Allow -Profile Any -Protocol TCP -RemoteAddress 192.168.1.100,192.168.1.101
Example: allowing VSPE to listen on all UDP ports and accept UDP packets from any external IP addresses
New-NetFirewallRule -DisplayName "VSPE UdpManager all ports" -Direction Inbound -Program "C:\Program Files\Eterlogic Software\Virtual Serial Ports Emulator (x64)\EterlogicVspeDeviceManagerService.exe" -Action Allow -Profile Any -Protocol UDP
Example: allowing VSPE to listen on all UDP ports and accept UDP packets only from specific remote IP addresses (192.168.1.100 and 192.168.1.101)
New-NetFirewallRule -DisplayName "VSPE UdpManager all ports" -Direction Inbound -Program "C:\Program Files\Eterlogic Software\Virtual Serial Ports Emulator (x64)\EterlogicVspeDeviceManagerService.exe" -Action Allow -Profile Any -Protocol UDP -RemoteAddress 192.168.1.100,192.168.1.101
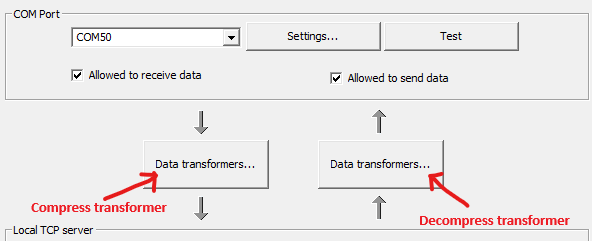
TCP server transformers for compression support
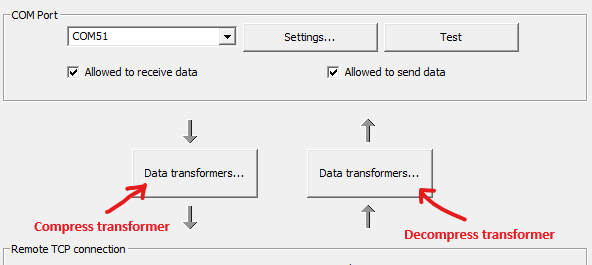
TCP client transformers for compression support
To add encryption/decryption to compressed traffic, you should add Encrypt data transformer (after Compress) to "TCP connection" flow and Decrypt data transformer to "COM port" flow (before Decompress).